84% of companies suffered an identity-related breach in the past year. Maintaining a least privilege security posture is critical to reducing the risk of a breach, and the blast radius of a successful attack.
Let Opal Security’s free least privilege security audit show you where you have risky access configured in your organization.
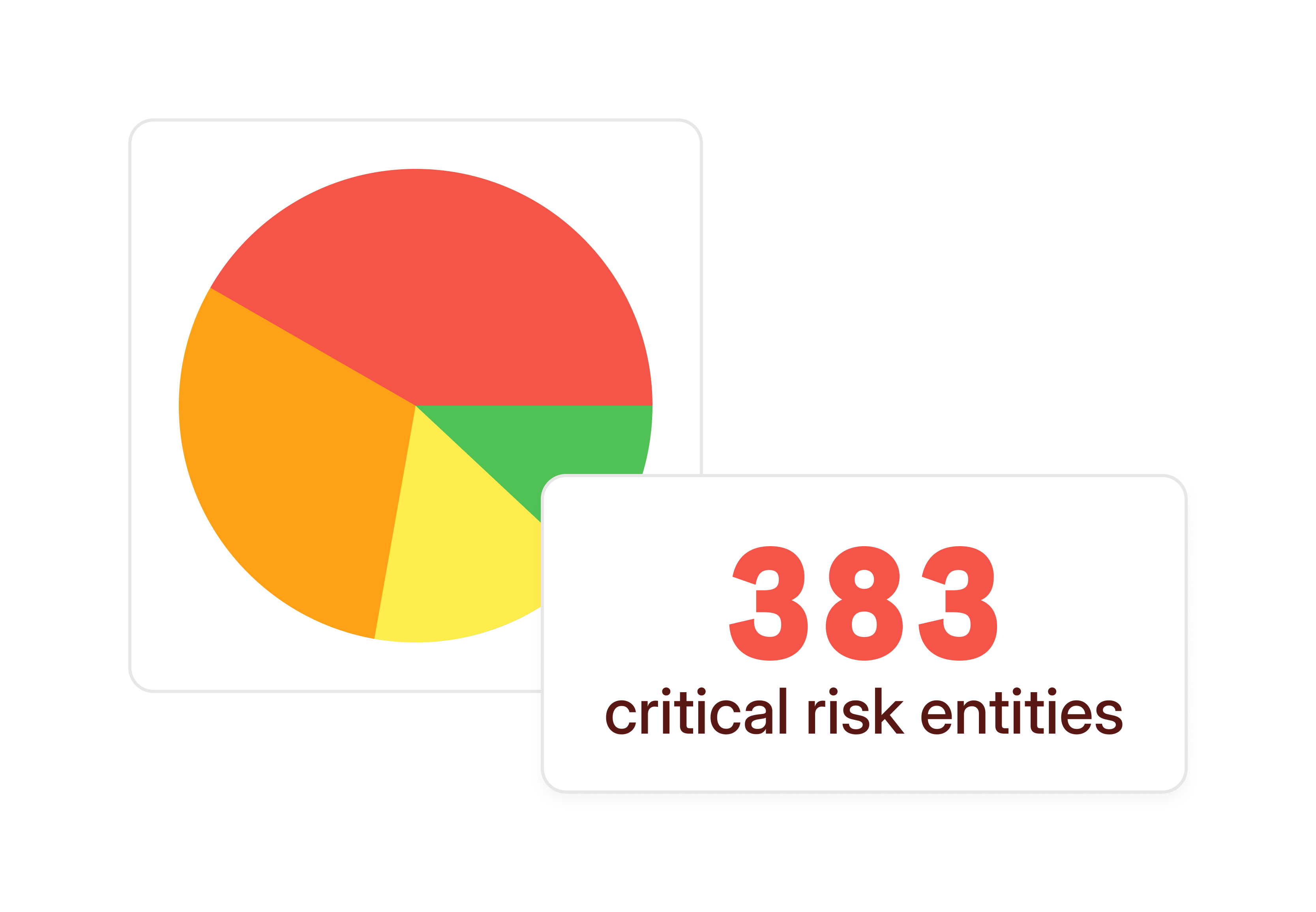
Receive a detailed report that not only highlights risks but also provides specific recommendations for remediation. See firsthand how Opal’s platform can help you achieve a least privilege posture.
.png?width=2000&name=urgent-threats%20(1).png)
Opal celebrates security leaders who want to embrace positive change, not check boxes.
Opal provides an efficient and intuitive solution for managing user access and access reviews. Opal's straightforward design and logically organized layout streamlines the process and allows me to quickly and easily understand what requires attention and why.

We wanted to increase our security posture by limiting who at our company had data to what, and Opal has been very effective at allowing us to do that as we grow quickly. Opal has become a critical part of our daily workflows. We use the Opal Slack feature a lot, and it's helped speed up access requests.

Opal has become a core pillar of our IAM strategy and is the primary method of granting access.

Implementing traditional access management solutions are typically large and complex projects with the potential to slow down employees. With Opal, enterprises can improve internal security posture and accelerate employee productivity.

Opal isn't just another security tool that produces too many warnings. Opal has enabled us to reduce risk by minimizing privilege across Engineering, while making it easy to obtain admin when needed. So far we've used it to minimize privilege on Kubernetes, IAM roles, breakglass, self-management of low-risk accounts, OpsGenie on-call integration, and the list goes on.

©2026 Acme Co, Inc. All rights reserved. Privacy Policy