Least Privileged Posture Management On-Demand Demo
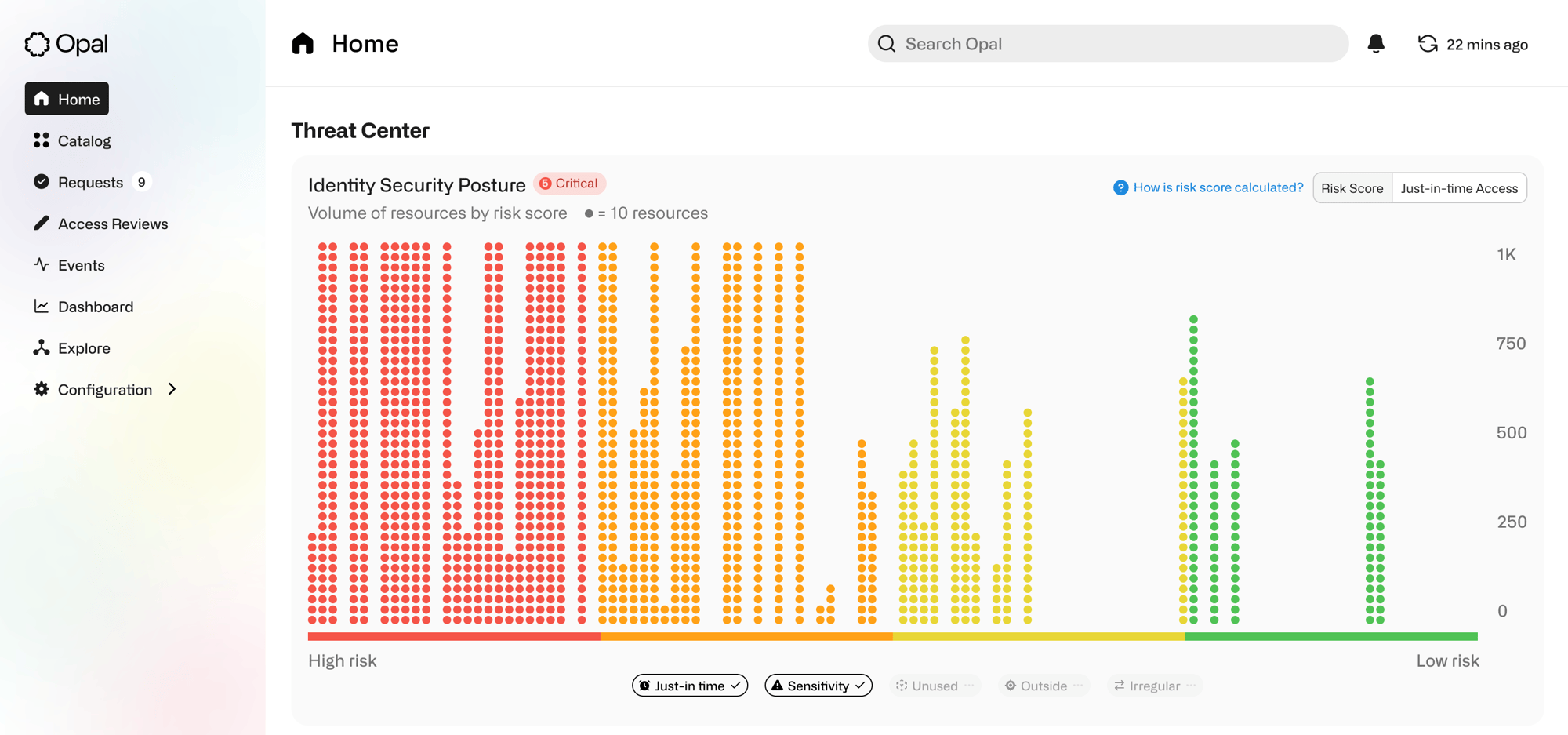
Opal Security’s identity security platform enables security and IT teams to provide least privileged access at scale in complex environments. Rather than gluing together multiple products - IGA, PAM, and CIEM tools and filling the cracks between them with manual effort and spreadsheets, Opal provides efficient coverage across your identity security program from a single, modern platform.
Watch this demo to learn how Opal Security can:
- Achieve birthright access
- Access risk analytics
- Provision just in time
- Automate user reviews
- Remediate in real-time
Fill Out This Form
About Opal Security
Opal Security offers a unified identity security solution, empowering complex businesses to manage access to critical systems and data. With Opal Security’s unique risk-driven approach, security and IT teams can remediate the most important issues quickly, control access at depth for greater precision, and implement user-friendly just-in-time workflows to prevent over-privileged access from growing. The platform enables least privilege access at scale across the enterprise, reducing overall risk, minimizing the blast radius of incidents, and ensuring compliance - without sacrificing enterprise growth.
